Monday, 21 April 2014
Chrome Remote Desktop for Android to Control Your PC from Anywhere
Have you ever been somewhere and urgently you need a file stored in your home computer ? This is very common situation that most of us deal with, but now rather returning home and get it, Google has offered a better solution for this problem.
Google – one of the most innovative tech companies on the planet, famous for providing new technologies to make every job easy for its users, has released Google's Chrome Remote Desktop service today for your Android Smartphones to remotely control your PC anytime, from anywhere.
Google’s Chrome Remote Desktop app for Android provides an easier and secure interaction of your computer with your Android Smartphones. So, using this app you can control your desktop system or PC remotely from anywhere using your Android Smartphone, provided your Mac, Windows or Linux system has Chrome Remote Desktop app installed and running.
Google first introduced this service in 2011, which allowed users of Chrome OS or Chrome browser to remotely access their personal computers back home in a free, easy and secure way and now they have released this feature for Android devices to make the same thing possible for Android users.
HOW TO USE IT
1. Install the Chrome Remote Desktop to your Chrome browser through the Chrome Web Store.
2. Open the app and Enable the remote connection service.
2. Open the app and Enable the remote connection service.
3. Set a minimum 6 digit pin code, as password.
4. Now Install 'Chrome Remote Desktop' Android app from Google Play Store.
4. Now Install 'Chrome Remote Desktop' Android app from Google Play Store.
5. Then you will see a list of PC’s that you can access. Just enter the respective PIN number to access it.
The new app even provides you to register multiple computers to your Android devices, so that you can control multiple systems on your single Smartphone or tablet AND a number of companies offer this ability like PhoneMyPC or TeamViewer.
For now, if you are using Android Smartphone or Tablet, you can download the free Remote Desktop Android App from the Google play store but for an iOS version it will be coming later this year.
19 Year Old Teenager Arrested for Exploiting Heartbleed Bug to Steal Data!
A teenager has been arrested by the Canadian police in relation to the infamous malicious breach on the country's taxpayer system using one of the most critical internet flaws, Heartbleed.
Heartbleed bug, that made headlines over past two weeks and every websites around the world flooded with its articles. Every informational website, Media and Security researchers are talking about Heartbleed, probably the biggest Internet vulnerability in recent history.
According to the Royal Canadian Mounted Police (RCMP), a 19-year-old 'Stephen Arthuro Solis-Reyes' of London, Ontario, is charged with the unauthorized access of the computer and criminal mischief in relation to the data breach of taxpayer’s private information from the Canada Revenue Agency (CRA) website.
“The RCMP treated this breach of security as a high priority case and mobilized the necessary resources to resolve the matter as quickly as possible,” Assistant Commissioner Gilles Michaud said in a statement.
“Investigators from National Division, along with our counterparts in ‘Ontario’ Division have been working tirelessly over the last four days analyzing data, following leads, conducting interviews, obtaining and executing legal authorizations and liaising with our partners,” he added.
After the public disclosure of Heartbleed bug on April 9, Solis-Reyes allegedly exploited this most critical security vulnerability, present in the OpenSSL of the CRA servers, to extract the private and sensitive information, including the social insurance numbers from the company’s system, before the computers were patched.
Heartbleed is a critical bug in the OpenSSL's implementation of the TLS/DTLS heartbeat extension that allows attackers to read portions of the affected server’s memory, potentially revealing users data, that the server did not intend to reveal.
Though there were allegations on the U.S. intelligence agency NSA of using the Heartbleed vulnerabilities from years to gather confidential information. But, this is the first known incident of hacker exploiting the critical internet Heartbleed bug to steal and compromise the data from the servers which are running on an affected OpenSSL version.
Exploiting the Heartbleed bug itself rarely leaves any traces, unless the attacker is not sending millions of heartbeats continuously from his own IP addresses. "The fact that they were able to trace it back to someone implies that it is not the work of organized crime or a professional hacker. It would be someone of very low skill." said Mark Nunnikhoven, Trend Micro.
Exploiting the Heartbleed bug itself rarely leaves any traces, unless the attacker is not sending millions of heartbeats continuously from his own IP addresses. "The fact that they were able to trace it back to someone implies that it is not the work of organized crime or a professional hacker. It would be someone of very low skill." said Mark Nunnikhoven, Trend Micro.
Solis-Reyes was arrested at his residence without incident on April 15 and is scheduled to appear in court in Ottawa on July 17, 2014, RCMP reported. The police also seized computer equipment from his residence, while the investigation is ongoing.
ZeuS Botnet Updating Infected Systems with Rootkit Equipped Trojan

ZeuS, or Zbot is one of the oldest families of financial malware, it is a Trojan horse capable to carry out various malicious and criminal tasks and is often used to steal banking information. It is distributed to a wide audience, primarily through infected web pages, spam campaigns and drive-by downloads.
Earlier this month, Comodo AV labs identified a dangerous variant of ZeuS Banking Trojan which is signed by stolen Digital Certificate belonging to Microsoft Developer to avoid detection from Web browsers and anti-virus systems.
FREE! FREE! ZeuS BRINGS ROOTKIT UPDATE
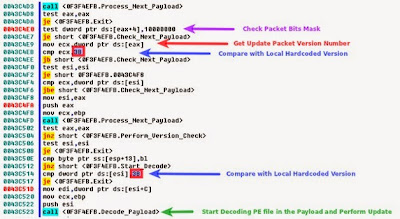
Recently the security researcher, Kan Chen at Fortinet has found that P2P Zeus botnet is updating its bots/infected systems with updates version that has the capability to drop a rootkit into infected systems and hides the trojan to prevent the removal of malicious files and registry entries.
The new variant also double check for the earlier installed version (0x38) of ZeuS trojan on the infected system and then replaces it with updated binary files (0X3B version).
“Every P2P Zeus binary would extract the version number from the update packet and compare the version number that is hardcoded in its body” to verify the success of update process.
According to researchers, there is only a minimal change in the new variant of P2P Zeus as the new binary also drops a rootkit driver file into the %SYSTEM32%\drivers folder, apart from its original functions. New Zeus Trojan equipped with rootkit feature makes it more sophisticated and increases the difficulty of removing Zeus from infected systems.
HOW TO PROTECT YOURSELF FROM ZeuS TROJAN
- We recommend users to use common sense and think twice before giving a click to any link on their e-mails or at any other websites they visit.
- Trustworthy companies don't send attachments unless you have requested specific documents. So, always use caution if you receive any email from an unknown contact with attachments that you haven't requested and do not bother to open it.
- Install a best Internet Security Tool and Configure the firewall to maximize the security of your computer system.
BJP leader LK Advani's Website Hacked
File photo of LK Advani
New Delhi: The official website of veteran BJP leader LK Advani was hacked today allegedly by Pakistani hackers who posted messages of "free-Kashmir" on the portal.
The hacker, who called himself Muhammad Bilal TeaM Pak Cyber Experts wrote "Pakistan Zindabad" messages on the site and called for an end to militarised governance in Kashmir.
The hacking comes close on the heels of a claim by Kashmiri separatist leader Syed Ali Shah Geelani that Narendra Modi had sent two emissaries to him.
Muhammad Bilal, the hacker, began his message by saying, "Good Morning Narendra Modi" and went on to raise the Kashmir issue.
The message posted on the site terms freedom of Kashmir as the goal of those who hacked Mr Advani s website lkadvani.in.
Meanwhile, Mr Advani, who was in Tamil Nadu today campaigning for the party in Vellore, was not aware of the hacking. None of his associates accompanying him or people at his residence knew of the development.
Site Link : lkadvani.in
Mirror Link : http://www.pak-zone.com/mirror.php?id=1099
Thursday, 17 April 2014
Google Admits that It Reads your Email's
Google has updated its privacy terms and conditions on Monday to offer more transparency regarding its email-scanning practices. One of the world’s biggest Web internet giant, Google, made it clear that the information its users submit and share with its systems is all analyzed.
Last year, Google was accused of its illegal interception of all electronic communications sent to Gmail account holders and using the gathering data to sell and place advertisements in order to serve related ads to its users. Practically, the more information you let Google collect about you, the more accurate its adverts become.
But Google has long insisted that its scanning practices are outlined in its terms of service.
So, finally admitting the accusation, Google has made some changes in its terms of service res a new paragraph that explains the manner in which its software automatically scans and analyzes the content of Gmail messages when they are sent, received, and stored.
"Our automated systems analyses your content (including emails) to provide you personally relevant product features, such as customized search results, tailored advertising and spam and malware detection," reads Google's updated terms. "This analysis occurs as the content is sent, received, and when it is stored."
Google said the changes were purposed to make the company's privacy policy easier to understand by users. "Today's changes will give people even greater clarity and are based on feedback we've received over the last few months," the company said in a statement.
Google's terms of service clearly states, "When you upload, or otherwise submit, store, send or receive content to or through our Services, you give Google (and those we work with) a worldwide license to use, host, store, reproduce, modify, create derivative works (such as those resulting from translations, adaptations or other changes we make so that your content works better with our Services), communicate, publish, publicly perform, publicly display and distribute such content."
Despite several accusations of violating privacy and wiretapping laws, Google won an important case last month when a federal judge dismiss most of a lawsuit against Google over accusations.
Lucy Koh, a United States District Court judge in San Jose, had consented to having their e-mail read for the purposes of targeted advertising, allowing for a potential class-action suit against the company.
Unfortunately there's no way to stop Google scanning your inbox to serve adverts...
Tuesday, 15 April 2014
FBI facial recognition database to have 52 Millions Photo's by next year!

The Recent documents obtained by EFF in response to our Freedom of Information Act lawsuit for information on Next Generation Identification (NGI) shows that the FBI's Next Generation Identification (NGI) database will contain 52 million photos by 2015. which is almost equal to one-third of of the US population.
By the middle of 2013 FBI already had 16 million images to its facial recognition database, report suggests that the database will be capable of processing 55,000 direct photo enrollments daily and of conducting tens of thousands of searches every day.
what came to be more shocking was that in addition to 46 million criminal images NGI will also include 4.3 million civil images to its database. so the images will be from both Criminal and Non-Criminal nature.
NGI already contains over 100 million individual records and has been designed to include multiple forms of biometric data, including palm prints, finger prints and iris scans in addition to face recognition data. with which other personal details is used to create personal files of Individuals. this is then shared by state, tribal, local and other Federal Authorities across the United states.
However the Question which rises now is why FBI needs Images of ( 4.3 Million peoples ) who are not involved in any Criminal case.....
While this database can be used to help law enforcement agencies and improve the Consumers, business and other Organisations it also can cause a innocent to come into the list of suspect for a criminal case.
it's unclear how such a big database will be managed,, and what oversights already exist in the planning....
since the recent NSA mass surveillance leaks people are more concerned about their privacy and now this may upset them more.
Monday, 14 April 2014
Labels:
Cyber News

Read More
Flickr vulnerable to SQL Injection and Remote C0de Execution Flaw
Yahoo-owned Flickr, one of the biggest online photo management and sharing website in the world was recently impacted by critical web application vulnerabilities, which left website's database and server vulnerable hackers.
Ibrahim Raafat, a security researcher from Egypt has found SQL injection vulnerabilities on Flickr Photo Books, new feature for printing custom photo books through Flickr that was launched 5 months ago.
He claimed to have found two parameters (page_id , items) vulnerable to Blind SQL injection and one (i.e.order_id) Direct SQL Injection that allowed him to query the Flickr database for its content by the injection of a SQL SELECT statements.
A Successful SQL exploitation could allow an attacker to steal the Database and MYSQL administrator password.
Furthermore, Flickr's SQL injection flaws also facilitate the attacker to exploit remote code execution on the server and using load_file(“/etc/passwd“) function he was successfully managed to read the content from the sensitive files on the Flickr server, as shown below:
In addition to this, Ibrahim was able to write new files on the server that let him upload a custom 'code execution shell'.
Video Demonstration:
He reported the vulnerability to Yahoo which have been patched.
Sunday, 13 April 2014
Labels:
Cyber News

Read More
MANY FILGHTS WERE CANCELED DUE TO THE DDOS ATTACK BY ANONGHOST and ANONSEC HACKERS (OPISRAEL)
As the opisrael is continued on second day,as anonghost and anonsec hackers attacked on airport websites which made cancellations many flights for several hours though some flights were delayed,and radars of airport were also jammed,which makes airports ideal place.we seems this is a largest cyber war on israeli cyberspace.Almost 80% websites are attacked by anonghost and anonsec hackers(opisrael 2014)
.as they said this war will ended on 10th of april 2014 according to the world time....
Saturday, 12 April 2014
Labels:
Cyber News


Read More
Researchers Get $10,000 for Hacking Google Server with Malicious XML!!

A critical vulnerability has been uncovered in Google that could allow an attacker to access the internal files of Google’s production servers. Sounds ridiculous but has been proven by the security researchers from Detectify.
The vulnerability resides in the Toolbar Button Gallery (as shown). The team of researchers found a loophole after they noticed that Google Toolbar Button Gallery allows users to customize their toolbars with new buttons. So, for the developers, it is easy to create their own buttons by uploading XML files containing metadata for styling and other such properties.
This feature of Google search engine is vulnerable to XML External Entity (XXE). It is an XML injection that allows an attacker to force a badly configured XML parser to "include" or "load" unwanted functionality that can compromise the security of a web application.
“The root cause of XXE vulnerabilities is naive XML parsers that blindly interpret the DTD of the user supplied XML documents. By doing so, you risk having your parser doing a bunch of nasty things. Some issues include: local file access, SSRF and remote file includes, Denial of Service and possible remote code execution. If you want to know how to patch these issues, check out the OWASP page on how to secure XML parsers in various languages and platforms," the researchers wrote on a blog post..
Using the same, the researchers crafted their own button containing fishy XML entities. By sending it, they gain access to internal files stored in one of Google's production servers and managed to read the “/etc/passwd” and the “/etc/hosts” files from the server.
By exploiting the same vulnerability the researchers said they could have access any other file on their server, or could have gain access to their internal systems through the SSRF exploitation.
The researchers straight away reported the vulnerability to the Google’s security team and rewarded with $10,000 (€7,200) bounty for identifying an XML External Entity (XXE) vulnerability in one of the search engine’s features.
Friday, 11 April 2014
Labels:
Vulnerability

Read More
How to Protect yourself from the "Heartbleed" Bug
Millions of websites, users' passwords, credit card numbers and other personal information may be at risk as a result of the Heartbleed security flaw, a vulnerability in widely used cryptographic library 'OpenSSL'.
Netcraft survey says that about half a million widely trusted active websites on the internet are vulnerable to the heartbleed bug, which means the information transmitting through hundreds of thousands of websites could be vulnerable, despite the protection offered by encryption techniques.
According to Netcraft, “the heartbeat extension was enabled on 17.5% of SSL sites, accounting for around half a million certificates issued by trusted certificate authorities. These certificates are consequently vulnerable to being spoofed (through private key disclosure), allowing an attacker to impersonate the affected websites without raising any browser warnings.”
Among the trusted names running OpenSSL is Yahoo!, which has been affected by this critical flaw. Yes, Yahoo Inc., which boasts more than 800 million users worldwide, is among the Internet services that could be potentially hurt by Heartbleed.
The bug leaks the below given information, although Yahoo! has since patched its systems.
The Popular sites which exhibit support for the TLS heartbeat extension also include Twitter, Facebook, GitHub, Bank of America, DropBox are not currently vulnerable, but it is unclear that they were vulnerable few days ago.
Including Yahoo!, Flickr, Tumbler, Google, OKCupid and even the anonymous search engine DuckDuckGo was vulnerable, which has now been fixed.
Yahoo Inc. said that it has "successfully made appropriate corrections" to the main Yahoo properties, including Yahoo Homepage, Search, Mail, Finance, Sports, Food, Tech, Flickr and Tumblr.
You can see the Heartbleed mass-test when performed around 8th April from here. In the list, the websites shown vulnerable may not be vulnerable right now.
HOW TO PROTECT YOURSELF FROM HEARTBLEED
First of all check if the sites you use every day on an individual basis are vulreble to Heartbleed bug or not using http://filippo.io/Heartbleed/, and if you're given a red flag, avoid the site for now. LastPass also created a Web app that will tell you what kind of encryption a site uses, and when the encryption was last updated.
If the site you use is not affected by the vulnerability, its good idea that you change your password immediately, assuming that it was vulnerable before, just to make sure that you are now safe. But changing the password before the bug is fixed could compromise your new password as well.
You are advised to don't reuse the same passwords on different websites and try to use a separate password for each website.
If you are using a public Wi-Fi at MacDonald or any other public places, then you should limit your Internet behavior and avoid sign in into websites that are especially sensitive.
OpenSSL version 1.0.1 through 1.0.1f and 1.0.2-beta1 are Vulnerable and flaw is fixed in OpenSSL 1.0.1g. If you haven't yet, please update your system that use OpenSSL for TLS encrypted communications.
And last but not the least; keep an eye on every financial transaction, and it is good practice to use two-factor authentication, which means with the password, the account requires a freshly generated pass code that shows up only on your personal smartphone, before getting into certain sites.
Wednesday, 9 April 2014
Labels:
Cyber News
Read More
iPhone 5s Users Fooled By Apple, NSA and A Fake middle finger
Last week Apple releases the iPhone 5S with Touch ID, a fingerprint-scanning feature, promoted by the company as "Your fingerprint is one of the best passwords in the world".
Just after the launch of iOS7, Hackers around the world come up with a series of security issues andprivacy concerns.
One of the most embarrassing hack released yesterday, when a group of German Hackers fooled the iPhone's biometric fingerprint security by just using a high resolution photo of someone’s fingerprint.
Now, We all are aware about many secret surveillance projects of NSA like PRISM, where U.S.government is collecting data from these Internet companies including - Apple.
Apple claimed that, iPhone will never upload fingerprints to their server, but can we believe them anymore ?
It is already proven that, During Surveillance operations and for Backup purpose, Smartphone applications can upload anything from your device to their online servers without any special permission or user interaction, So why they will not upload your Fingerprint scans too ??
In Only this weekend, over 9 million new iPhones devices sold in International Market. In the name of stopping terrorism, NSA now manages to create a database of Fingerprints, of more than 9 million users, which will turn billions in a month.
Labels:
Vulnerability
Read More
Heartbleed - OpenSSL Zero-day Bug leaves Millions of websites Vulnerable
It is advised to those who are running their web server with OpenSSL 1.0.1 through 1.0, then it is significantly important that you update to OpenSSL 1.0.1g immediately or as soon as possible.
As this afternoon, an extremely critical programming flaw in the OpenSSL has been discovered that apparently exposed the cryptographic keys and private data from some of the most important sites and services on the Internet.
The bug was independently discovered by security firm Codenomicon along with a Google Security engineer. The flaw is in the popular OpenSSL cryptographic software library and its weakness allows cyber criminals to steal the information protected, under normal conditions, by the SSL (Secure Sockets Layer) or TLS (Transport Security Layer) encryption used to secure the Internet.
OpenSSL is an open-source implementation of the SSL and TLS protocols. The core library implements the basic cryptographic functions that enable SSL and TLS encryption. Mostly every websites use either SSL or TLS, even the Apache web server that powers almost half of the websites over internet utilizes OpenSSL.
HEARTBLEED BUG
The discoverer of the vulnerability dubbed the bug as ‘Heartbleed bug’, as the exploit rests on a bug in the implementation of OpenSSL’s TLS/DTLS (transport layer security protocols) heartbeat extension (RFC6520).
This critical bug with code ID CVE-2014-0160, could allows an attacker to expose up to 64kB of memory from the server or a connected client computer running a vulnerable version of OpenSSL software. Specifically, this means that an attacker can steal keys, passwords and other private information remotely.
“We have tested some of our own services from attacker’s perspective. We attacked ourselves from outside, without leaving a trace. Without using any privileged information or credentials we were able steal from ourselves the secret keys used for our X.509 certificates, usernames and passwords, instant messages, emails and business critical documents and communication.”
The vulnerability in the OpenSSL’s transport layer security (TSL) protocols’ heartbeat section has been in the wild since March 2012 and is supposed to be even more dangerous than Apple’s recent SSL bug, which outcropped the possibility for man-in-the-middle (MitM) attacks.
As the Heartbleed bug reveals encryption keys that could lead to other compromises, affects past traffic and may affect as much as 66 percent of Internet websites over the internet. 10 out of top 1000 sites are vulnerable to this flaw, including Yahoo Mail, Lastpass and the FBI site. There also is a proof-of-concept exploit for the flaw posted on Github. On this website, you can check if your web server is vulnerable or not.
"Bugs in single software or library come and go and are fixed by new versions," the researchers who discovered the vulnerability wrote in a blog post published Monday. "However this bug has left a large amount of private keys and other secrets exposed to the Internet. Considering the long exposure, ease of exploitations and attacks leaving no trace this exposure should be taken seriously."
Fixes for the bug have been released by the researchers. So, who are running the OpenSSL 1.0.1f version may update to OpenSSL 1.0.1g
Monday, 7 April 2014
Labels:
Cyber News

Read More
Pakistani Hacker Arrested for Hacking Telecom Company Database

Pakistan’s Federal Investigation Agency (FIA) has arrested a Pakistani Hacker allegedly involved in hacking into a telecom company and uploaded their database on his website.
With the help of the National Response Center for Cyber Crime (NR3C) of Pakistan’s Federal Investigation Agency, the local authorities were able to trace and arrest the hacker suspected of infiltrating into the systems of Warid Telecom, an Abu-Dhabi-based telecoms company that provides services in Congo, Pakistan and Uganda.
The suspect, Mubashar Shahzad, a resident of Kasur, is believed to have downloaded Warid Telecom’s customer information from the company’s databases and exposed it online, which was published onearlysms.com, a site hosted with HosterPK.
Investigation started after one of the senior manager of a cellular company filed a complaint saying the ‘information of its consumers till 2006 had been exposed over the internet.’
“A technical/forensic analysis found that the website was being hosted by hosterpk. The FIA traced the IP address, email address and phone number of the suspect through the host company,” Usman Anwar, the Director of FIA, told The Express Tribune...
The suspects IP address was traced to a shop in Ghalla Mandi, Kasur, from where the authorities arrested the suspect Mubashar Shahzad. The Investigation Team also detected and seized Shahzad’s computers which contained folders named ‘Warid Data’. In addition to that, two desktop systems, hard drives and portable Hard drives were also seized by the authorities.
The website on which the stolen data was posted by the hacker has now been shut down.
Sunday, 6 April 2014
Labels:
Cyber News
Read More
Worst Data Breach in German History 18 Million Email Passwords Compromised
Germany has confirmed its biggest Data theft in the country's history with usernames and passwords of some 18 million email accounts stolen and compromised by hackers.
The Story broke by the German press, Der Spiegel on Thursday, when German Authorities revealed another mass hacking of private data belonged to German citizens and major Internet companies both in Germany and abroad.
16 MILLION AND NOW 18 MILLION
Authorities in the northwestern city of Verden unearthed a treasure of personal information, a list of about 18 million stolen email addresses and passwords, and seized it just after only two months from the previous major data breach, when researchers came across 16 million compromised email accounts of German users while conducting research on a botnet, a network of computers infected with malware.
The accounts were compromised by hackers in the mid of January, and Der Spiegel suggests that the same group of hackers is responsible for both thefts and that they may be based in one of the Baltic countries.
MILLION ON SPAM .. SHOP... THEFT !!!
According to Investigators, some of the accounts are used to send spam emails and some combinations of email and password are used for online shopping portals, as these mass of stolen personal information could also be used to obtain the financial details of users account.
To help in securing the Internet users, German authorities warned to take additional security measures to prevent cyber criminals using their data while shopping online.
"It is suspected that these stolen records are being actively misused," said Lutz Gaebel, spokesman of the prosecutor's office in Verden.
SOURCE OF DATA
Till now, It has not been revealed by the investigators that how much they know about this massive data Breach and How the attackers get their evil hands on the personal data of over 18 million users. Lutz Gaebel declined to give more information due to the ongoing investigation.
It is estimated that at least three million of the accounts belonged to German citizens and some of the compromised email accounts have international domain extensions such as ‘.COM’. But in real, the number could be much larger than the visible one as the investigation is ongoing.
The German prosecutor investigating the latest major data theft informed the country's IT watchdog, Federal Office for Information Security (BSI), to introduce additional security measures to help the Internet users...
Subscribe to:
Posts
(
Atom
)