Monday, 21 April 2014
Chrome Remote Desktop for Android to Control Your PC from Anywhere
Have you ever been somewhere and urgently you need a file stored in your home computer ? This is very common situation that most of us deal with, but now rather returning home and get it, Google has offered a better solution for this problem.
Google – one of the most innovative tech companies on the planet, famous for providing new technologies to make every job easy for its users, has released Google's Chrome Remote Desktop service today for your Android Smartphones to remotely control your PC anytime, from anywhere.
Google’s Chrome Remote Desktop app for Android provides an easier and secure interaction of your computer with your Android Smartphones. So, using this app you can control your desktop system or PC remotely from anywhere using your Android Smartphone, provided your Mac, Windows or Linux system has Chrome Remote Desktop app installed and running.
Google first introduced this service in 2011, which allowed users of Chrome OS or Chrome browser to remotely access their personal computers back home in a free, easy and secure way and now they have released this feature for Android devices to make the same thing possible for Android users.
HOW TO USE IT
1. Install the Chrome Remote Desktop to your Chrome browser through the Chrome Web Store.
2. Open the app and Enable the remote connection service.
2. Open the app and Enable the remote connection service.
3. Set a minimum 6 digit pin code, as password.
4. Now Install 'Chrome Remote Desktop' Android app from Google Play Store.
4. Now Install 'Chrome Remote Desktop' Android app from Google Play Store.
5. Then you will see a list of PC’s that you can access. Just enter the respective PIN number to access it.
The new app even provides you to register multiple computers to your Android devices, so that you can control multiple systems on your single Smartphone or tablet AND a number of companies offer this ability like PhoneMyPC or TeamViewer.
For now, if you are using Android Smartphone or Tablet, you can download the free Remote Desktop Android App from the Google play store but for an iOS version it will be coming later this year.
19 Year Old Teenager Arrested for Exploiting Heartbleed Bug to Steal Data!
A teenager has been arrested by the Canadian police in relation to the infamous malicious breach on the country's taxpayer system using one of the most critical internet flaws, Heartbleed.
Heartbleed bug, that made headlines over past two weeks and every websites around the world flooded with its articles. Every informational website, Media and Security researchers are talking about Heartbleed, probably the biggest Internet vulnerability in recent history.
According to the Royal Canadian Mounted Police (RCMP), a 19-year-old 'Stephen Arthuro Solis-Reyes' of London, Ontario, is charged with the unauthorized access of the computer and criminal mischief in relation to the data breach of taxpayer’s private information from the Canada Revenue Agency (CRA) website.
“The RCMP treated this breach of security as a high priority case and mobilized the necessary resources to resolve the matter as quickly as possible,” Assistant Commissioner Gilles Michaud said in a statement.
“Investigators from National Division, along with our counterparts in ‘Ontario’ Division have been working tirelessly over the last four days analyzing data, following leads, conducting interviews, obtaining and executing legal authorizations and liaising with our partners,” he added.
After the public disclosure of Heartbleed bug on April 9, Solis-Reyes allegedly exploited this most critical security vulnerability, present in the OpenSSL of the CRA servers, to extract the private and sensitive information, including the social insurance numbers from the company’s system, before the computers were patched.
Heartbleed is a critical bug in the OpenSSL's implementation of the TLS/DTLS heartbeat extension that allows attackers to read portions of the affected server’s memory, potentially revealing users data, that the server did not intend to reveal.
Though there were allegations on the U.S. intelligence agency NSA of using the Heartbleed vulnerabilities from years to gather confidential information. But, this is the first known incident of hacker exploiting the critical internet Heartbleed bug to steal and compromise the data from the servers which are running on an affected OpenSSL version.
Exploiting the Heartbleed bug itself rarely leaves any traces, unless the attacker is not sending millions of heartbeats continuously from his own IP addresses. "The fact that they were able to trace it back to someone implies that it is not the work of organized crime or a professional hacker. It would be someone of very low skill." said Mark Nunnikhoven, Trend Micro.
Exploiting the Heartbleed bug itself rarely leaves any traces, unless the attacker is not sending millions of heartbeats continuously from his own IP addresses. "The fact that they were able to trace it back to someone implies that it is not the work of organized crime or a professional hacker. It would be someone of very low skill." said Mark Nunnikhoven, Trend Micro.
Solis-Reyes was arrested at his residence without incident on April 15 and is scheduled to appear in court in Ottawa on July 17, 2014, RCMP reported. The police also seized computer equipment from his residence, while the investigation is ongoing.
ZeuS Botnet Updating Infected Systems with Rootkit Equipped Trojan

ZeuS, or Zbot is one of the oldest families of financial malware, it is a Trojan horse capable to carry out various malicious and criminal tasks and is often used to steal banking information. It is distributed to a wide audience, primarily through infected web pages, spam campaigns and drive-by downloads.
Earlier this month, Comodo AV labs identified a dangerous variant of ZeuS Banking Trojan which is signed by stolen Digital Certificate belonging to Microsoft Developer to avoid detection from Web browsers and anti-virus systems.
FREE! FREE! ZeuS BRINGS ROOTKIT UPDATE
Recently the security researcher, Kan Chen at Fortinet has found that P2P Zeus botnet is updating its bots/infected systems with updates version that has the capability to drop a rootkit into infected systems and hides the trojan to prevent the removal of malicious files and registry entries.
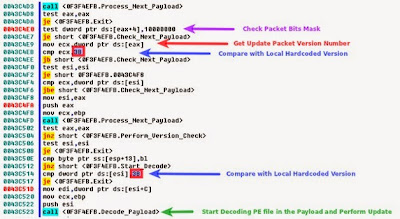
The new variant also double check for the earlier installed version (0x38) of ZeuS trojan on the infected system and then replaces it with updated binary files (0X3B version).
“Every P2P Zeus binary would extract the version number from the update packet and compare the version number that is hardcoded in its body” to verify the success of update process.
According to researchers, there is only a minimal change in the new variant of P2P Zeus as the new binary also drops a rootkit driver file into the %SYSTEM32%\drivers folder, apart from its original functions. New Zeus Trojan equipped with rootkit feature makes it more sophisticated and increases the difficulty of removing Zeus from infected systems.
HOW TO PROTECT YOURSELF FROM ZeuS TROJAN
- We recommend users to use common sense and think twice before giving a click to any link on their e-mails or at any other websites they visit.
- Trustworthy companies don't send attachments unless you have requested specific documents. So, always use caution if you receive any email from an unknown contact with attachments that you haven't requested and do not bother to open it.
- Install a best Internet Security Tool and Configure the firewall to maximize the security of your computer system.
BJP leader LK Advani's Website Hacked
File photo of LK Advani
New Delhi: The official website of veteran BJP leader LK Advani was hacked today allegedly by Pakistani hackers who posted messages of "free-Kashmir" on the portal.
The hacker, who called himself Muhammad Bilal TeaM Pak Cyber Experts wrote "Pakistan Zindabad" messages on the site and called for an end to militarised governance in Kashmir.
The hacking comes close on the heels of a claim by Kashmiri separatist leader Syed Ali Shah Geelani that Narendra Modi had sent two emissaries to him.
Muhammad Bilal, the hacker, began his message by saying, "Good Morning Narendra Modi" and went on to raise the Kashmir issue.
The message posted on the site terms freedom of Kashmir as the goal of those who hacked Mr Advani s website lkadvani.in.
Meanwhile, Mr Advani, who was in Tamil Nadu today campaigning for the party in Vellore, was not aware of the hacking. None of his associates accompanying him or people at his residence knew of the development.
Site Link : lkadvani.in
Mirror Link : http://www.pak-zone.com/mirror.php?id=1099
Thursday, 17 April 2014
Google Admits that It Reads your Email's
Google has updated its privacy terms and conditions on Monday to offer more transparency regarding its email-scanning practices. One of the world’s biggest Web internet giant, Google, made it clear that the information its users submit and share with its systems is all analyzed.
Last year, Google was accused of its illegal interception of all electronic communications sent to Gmail account holders and using the gathering data to sell and place advertisements in order to serve related ads to its users. Practically, the more information you let Google collect about you, the more accurate its adverts become.
But Google has long insisted that its scanning practices are outlined in its terms of service.
So, finally admitting the accusation, Google has made some changes in its terms of service res a new paragraph that explains the manner in which its software automatically scans and analyzes the content of Gmail messages when they are sent, received, and stored.
"Our automated systems analyses your content (including emails) to provide you personally relevant product features, such as customized search results, tailored advertising and spam and malware detection," reads Google's updated terms. "This analysis occurs as the content is sent, received, and when it is stored."
Google said the changes were purposed to make the company's privacy policy easier to understand by users. "Today's changes will give people even greater clarity and are based on feedback we've received over the last few months," the company said in a statement.
Google's terms of service clearly states, "When you upload, or otherwise submit, store, send or receive content to or through our Services, you give Google (and those we work with) a worldwide license to use, host, store, reproduce, modify, create derivative works (such as those resulting from translations, adaptations or other changes we make so that your content works better with our Services), communicate, publish, publicly perform, publicly display and distribute such content."
Despite several accusations of violating privacy and wiretapping laws, Google won an important case last month when a federal judge dismiss most of a lawsuit against Google over accusations.
Lucy Koh, a United States District Court judge in San Jose, had consented to having their e-mail read for the purposes of targeted advertising, allowing for a potential class-action suit against the company.
Unfortunately there's no way to stop Google scanning your inbox to serve adverts...
Subscribe to:
Comments
(
Atom
)